Hard appearance, comfortable feel
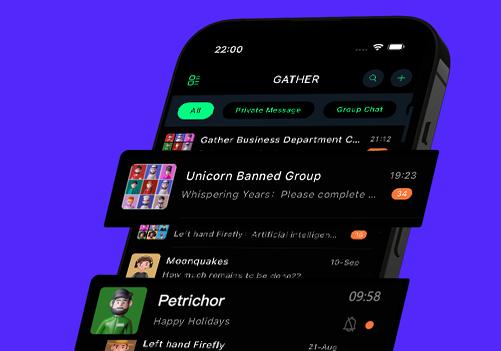
Deploy hardware boxes: G-Box in different countries around the world to provide a distributed and decentralized message exchange network



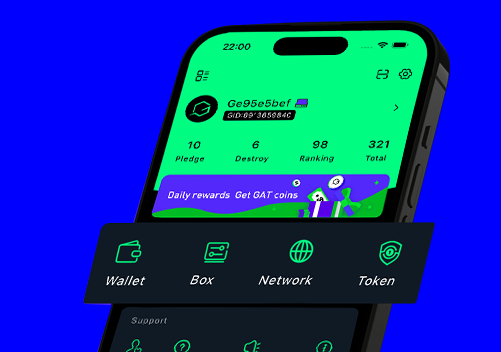
Integrate diverse chat, encrypted wallet, ecological applications and other modules
Open the mobile version of the App to start a new top-secret chat journey. Your privacy is only in your mobile phone.
Web3 basic public chain "born for application"
The first heterogeneous composite chain model, supporting multiple consensus algorithms to achieve dedicated chain dedicated application development, massive parallel computing and constant low-price handling fees.

Partner
Remote multi-data center architecture
Within 2 years, a number of stable data center custody hardware box (G-BOX) is built globally to improve the distributed computing capabilities of the product, and the geographical location is more faulty.

G-Box box
Each node provides network services and data exchange, temporary data storage and other functions

GAT instance chain
The instance chain provides the Gather ecological chain data, $ GAT token to empower ecology

GProto
Self-created network communication protocol, high performance and low power consumption

Gather applet
Open the window of ecological interconnection interconnection through a small program
Gather introduction video
Take a quick look at what Gather is?
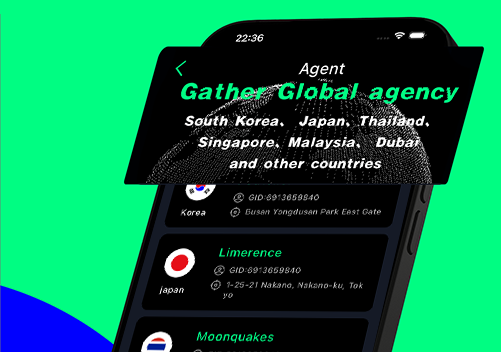
Global national agents jointly develop Goethe's cause
Activate each country's agent, play a leading role in the country, and push the operation of Gather products in the country
development and routes
Here, you can find the process of Gather's product and the future development route planning
Establish
- check_circle Project establishment
- check_circle Hong Kong company established
- check_circle Product introduction conference
- check_circle The first data center selection
Take root
- check_circle Gather Foundation was established
- check_circle Construction of Hong Kong Causeway Bay Club
- check_circle Kuala Lumpur Data Center Opening
- check_circle Gather App closed beta test launched
Target
- check_circle Recruit more national agents
- check_circle Asia R&D center completed
- check_circle Promote Gather's ecological development
- check_circle Foundation promotes project cooperation
The news is also exciting
Every new incident, new hotspot, new cooperation, and enjoy with you